Essential Eight Maturity Model
Proactive defence against cyber threats is key to your business’s cyber resilience, whether you’re at SME or enterprise level. Recommended by the ACSC (Australian Cyber Security Centre) for all Australian businesses, the Essential Eight is a collection of mitigation strategies that form a baseline for your cybersecurity. Adopting them will help your business stay ahead of the constantly evolving threat landscape. Smile IT is here to make your compliance with the Essential Eight easy and seamless. Let’s show you how!
WHAT IS THE ESSENTIAL EIGHT?
The below video gives a comprehensive breakdown of The Essential Eight. It’s a great introductory point if you’re learning about this framework and it’s eight strategies for the first time.
THE ESSENTIAL EIGHT STRATEGIES DEFINED
The Essential Eight is a risk management framework consisting of eight mitigation strategies. Each strategy is designed to either prevent attacks, limit attacks if they do happen, or recover data and applications in the event of an attack. Here are all eight:

Application Control
Only approved applications run within your systems, to prevent malicious code entering.

Patch Applications
Regularly update your applications and operating systems to reduce security vulnerabilities.

Configure Macro Settings
Only allow vetted Microsoft macros, to prevent malicious code from being executed.

User Application Hardening
Limit the functions of applications so it becomes harder for vulnerabilities to be exploited.

Restrict Administrative Privileges
Only trusted and authorsied individuals should have access to internal admin accounts.

Patch Operating Systems
Operating systems with security vulnerabilities should be patched within 48 hours.

Multi-Factor Authentication
Add an extra layer of protection to prevent access when passwords become compromised.

Regular Backups
Daily backups should be made and kept for three months, to ensure post-breach information access.
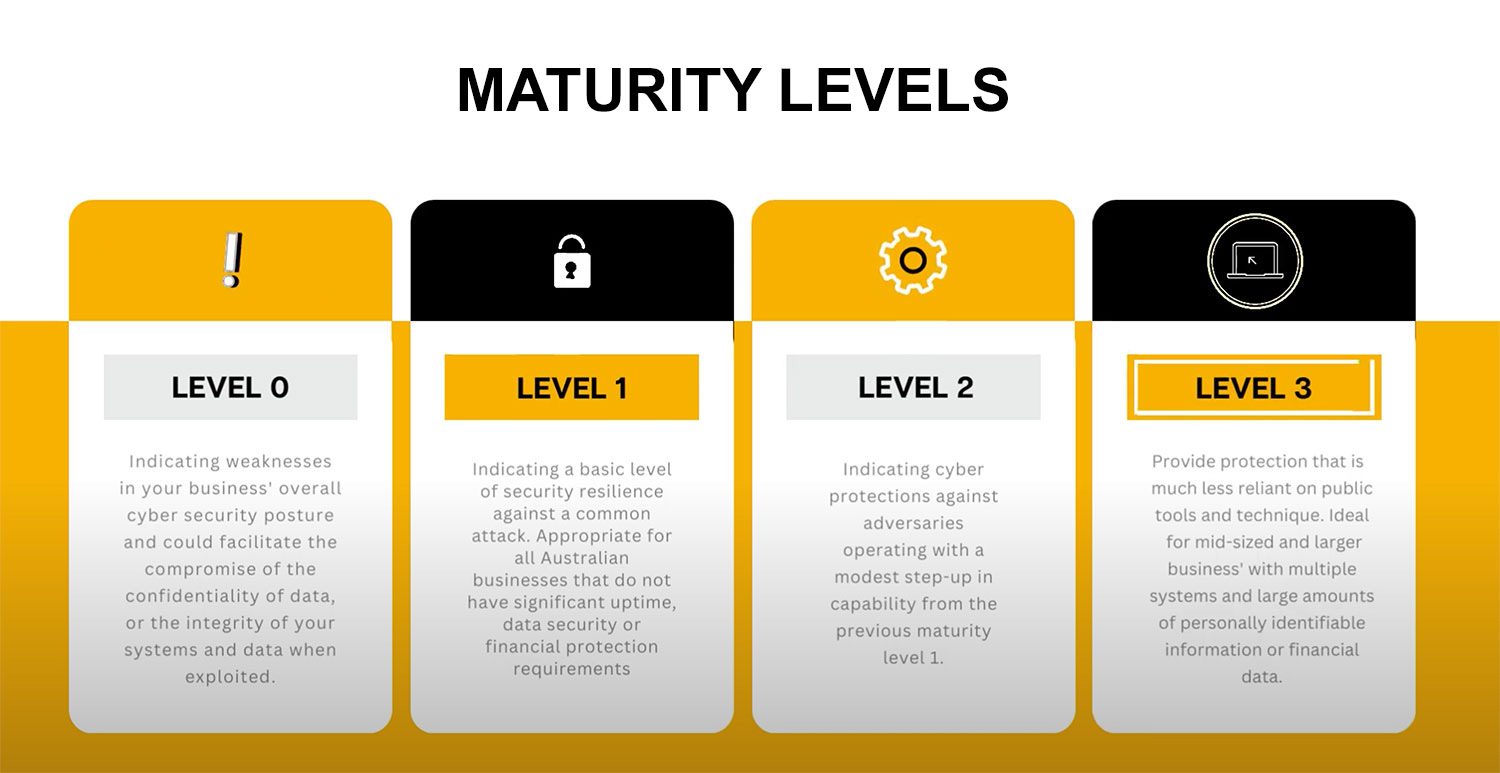
The Four Maturity Levels
Upon performing an Essential Eight audit of your cybersecurity, your organisation will be classified into one of four maturity levels. This maturity model allows you to assess how well you’re implementing the mitigation strategies of the Essential Eight, and in what areas you should improve. The four levels are as follows:
Level 0: Ad Hoc. You have no formal procedures or processes in place for implementing the recommended strategies. There is weakness in your overall cybersecurity posture.
Level 1: Developing. You have started to develop processes and procedures, although they are inconsistent and not fully integrated. A basic level of security is in place.
Level 2: Managing. You have consistent and integrated processes and procedures in place for Essential Eight implementation. Better cyber protection is a result.
Level 3: Embedding. The Essential Eight strategies are fully embedded into your operations. Adaptive protections help keep your organisation safe.
FREE ESSENTIAL EIGHT MATURITY ASSESSMENT TOOL
For many business owners, cybersecurity is an overwhelming and intimidating concept. The Essential Eight is extremely useful because it provides a standard against which to measure your organisation and a concrete guide on how to improve.
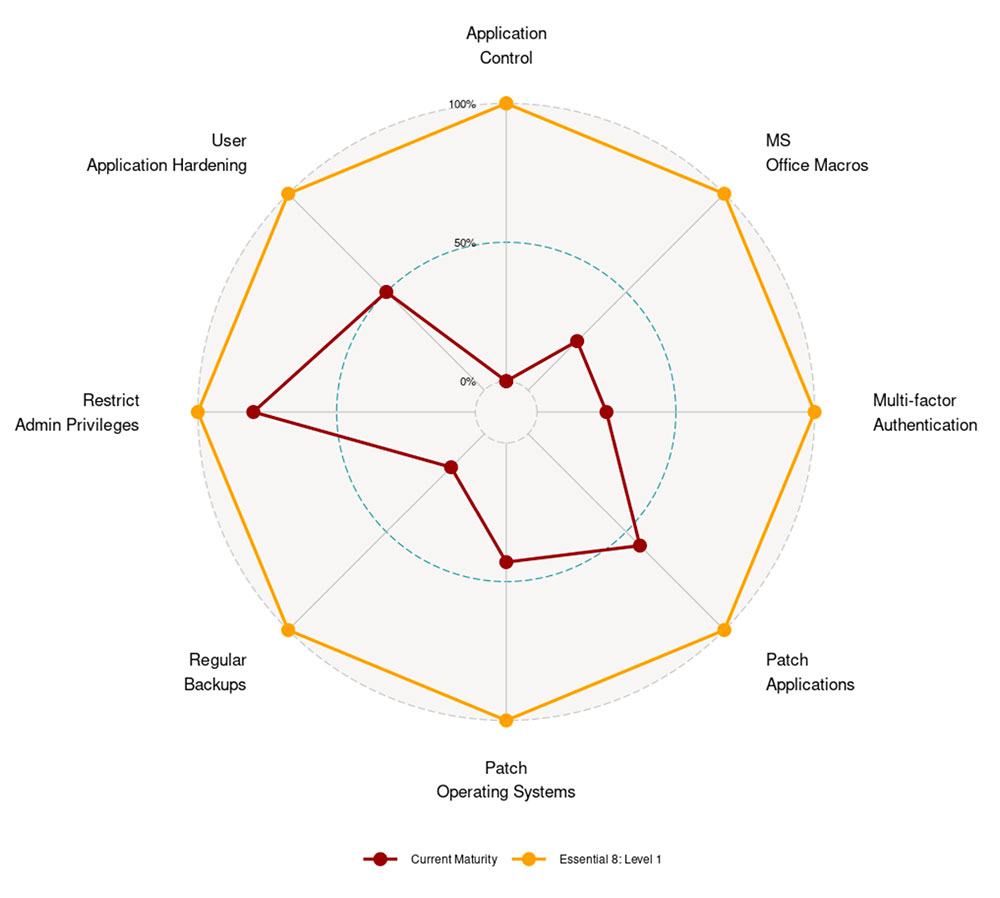
But where to begin with The Essential Eight? At Smile IT we want to take the overwhelm out of cybersecurity for you. We’ve used enterprise-grade software to come up with a self-assessment tool that’ll provide an instant overview of where you’re at in terms of reaching Level 1: Developing.
The tool involves answering a number of questions about your company-wide operations and processes. A comprehensive report is then generated, detailing where your organisation stands with each of the eight strategies. As an overview, a spider diagram clearly illustrates how far you are towards achieving Level 1 Maturity. Look right for an example!
Why not give this Essential Eight Tool a whirl now? You’ll get a powerful insight into your company’s cybersecurity posture, and it won’t cost you anything.
TRY THE ESSENTIAL EIGHT SELF ASSESSMENT TOOL FOR FREE
WHAT COMES AFTER THE ESSENTIAL EIGHT AUDIT?
Cybersecurity doesn’t have any ‘set and forget’ solutions. The Essential Eight isn’t a framework you implement with nothing more to do. Maintaining a resilient and cyber-healthy organisation using these eight strategies is an ongoing process of staying ahead of the latest threats, keeping up to date with the latest protection and maintaining strict vigilance at all times.
It seems like a lot because it is. And that’s where we can help. Getting to grips with the Essential Eight is challenging, and remaining compliant with the strategies even more so.
Smile IT is trusted by government agencies, international organisations and a whole spectrum of Australian businesses with their cyber security. We’d love to get you up to speed to with the Essential Eight. Get in touch via the form below, or why not give our free Essential Eight Assessment tool a go?
NEED CYBER SECURITY GUIDANCE?
Smile IT is here to assess your Essential Eight compliance and guide you to an improved cybersecurity posture. Get in touch using the form below and let’s get started!
