Today we’re talking about the second of the ACSC Essential Eight cybersecurity mitigation strategies, ‘Patch Applications’.
Patching is an incredibly important but often overlooked part of keeping your organisation safe. It’s not just one of those IT tasks that doesn’t need much attention – keeping your applications up to date with the latest patches is essential if you’re going to stop hackers breaching your defences.
If you and your team aren’t on top of it, you could be leaving the door to your network and systems wide open. Today we’re going to look at what application patching is, and why it’s such an important part of the Essential Eight.
What Does Application Patching Mean?
A patch is simply a fix. Developers release them regularly to correct bugs, improve performance and fix security holes. Patching your applications means applying those fixes.
Software code is complex and can often contain flaws. These flaws can in turn become security vulnerabilities – gateways for hackers to exploit. They can vary from the minor to the critical – but be sure that hackers are always on the lookout for them.
If they know there’s a flaw in the code, they’re going to come after it. If your applications aren’t patched, they’ll exploit them.
Why Is Patching Important?
It all boils down to timeframes. Once a vulnerability becomes public (and that happens fast), attackers move quickly. They create automated tools that scan the internet for systems that haven’t applied the latest patch. If your business is one of them, you’re now a target.
According to the Australian Cyber Security Centre (ACSC), attackers often exploit these vulnerabilities within 48 hours of a patch being released. That’s not a lot of time, especially if you’ve got a manual or inconsistent patching process.
A single unpatched application can compromise your whole network, which can lead to serious consequences like data breaches, downtime, and reputational damage. Legal issues can also arise if customer information is involved.
Recommended Timeframes for Applying Patches
If a known vulnerability in an applications code has become public, don’t delay in applying the patch as soon as it becomes available. Here are the guidelines from the ACSC, based on the level of cyber threat your organisation faces:
For basic threat environments:
- Internet-facing services: Apply patches within 14 days or within 48 hours if an exploit is publicly known.
- Frequently targeted applications: Patch within one month.
For moderate threat environments:
- Internet-facing services: Apply updates within 14 days, or 48 hours if an exploit is circulating.
- Common targets (like web browsers or office apps): Patch within two weeks.
- All other applications: Ensure patches are applied within a month.
For advanced threat environments:
- Internet-facing services and commonly targeted applications: Patches should be deployed within 48 hours if exploited — otherwise, within two weeks.
- Other applications: Apply updates within one month.
Common Challenges Businesses Face
Many businesses struggle to keep up with patching their applications. Some of the challenges reported to Smile IT include:
- Too many applications to manage: Between desktops, laptops, mobiles, and servers, it’s hard to keep track.
- Manual processes: If you’re relying on someone to check for updates and apply them manually, you’ll fall behind.
- Compatibility concerns: Sometimes patches can cause issues with other software, making businesses hesitant to apply them quickly.
- Lack of visibility: You don’t know what’s out of date unless you’re actively scanning and tracking patch status across your systems.
Best Practices for Application Patching
Want to make patching a strength instead of a struggle? Here are a few best practices we recommend:
1. Automate Where You Can
Use automated patch management tools to handle regular updates. They can scan your network, deploy patches, and report on success rates.
2. Maintain an Inventory
Know what you’re running. Keep a list of all applications and versions across your systems so you’re not blindsided when an update is released.
3. Test First
For mission-critical applications, test patches in a controlled environment before rolling them out. This helps catch compatibility issues before they impact your users.
4. Set Patching Schedules and Escalation Paths
Create a regular patching schedule for less critical updates and define an emergency process for critical ones that need to be applied within 48 hours.
5. Don’t Ignore Third-Party Apps
It’s not just Microsoft Office or Google Chrome that need patching. Any third-party software you use such as PDF readers, design tools, and ERP platforms can become a risk if left unpatched.
Application Patching and Maturity Levels
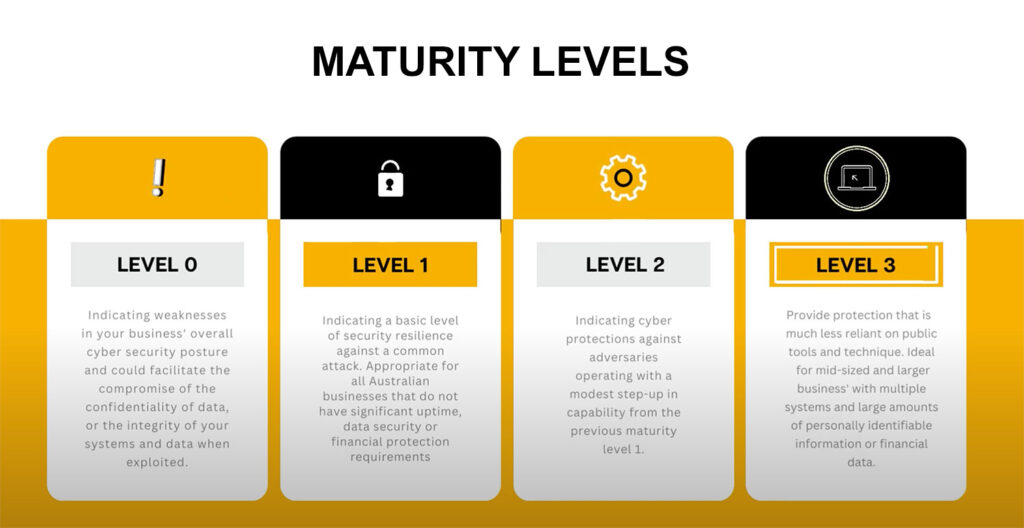
The Essential Eight has four maturity levels that indicate how well your organisation is applying the mitigation strategies it recommends. Level 0 indicates no formal procedures or processes in place, while levels 1 to 3 show an increasing adoption of the Essential Eight strategies. The image above sums up the four levels.
Here’s how patch application looks for the three maturity levels above 0.
Maturity Level One
At this foundational level, organisations need to:
- Apply patches for vulnerabilities in commonly used software (such as office suites, web browsers and their extensions, email clients, PDF readers, Adobe Flash Player, and security tools) within one month of release.
- Run vulnerability scans on the above applications at least every two weeks.
- Remove unsupported or obsolete software, particularly from internet-facing systems and frequently used applications, to reduce exposure to unpatched vulnerabilities.
Maturity Level Two
A more advanced approach is adopted at Maturity Level Two:
- Patching and vendor-recommended mitigations must be extended to all applications within the environment, with updates applied within one month of release.
- Vulnerability scanning must be performed at least fortnightly across all applications, not just those commonly targeted.
- For higher-risk software like office productivity tools, browsers, email clients and PDF readers, scanning frequency should increase to a weekly cadence.
Maturity Level Three
This level requires proactive and fast-acting measures:
- Vulnerabilities in key applications, such as browsers, office software, email clients, and PDF readers, must be patched within two weeks of detection, or within 48 hours if an exploit is being used in the wild.
- Any software that’s no longer supported by the vendor must be fully removed from the environment, ensuring there are no weak links in the application stack.
Smile IT and the Essential Eight
At Smile IT we’re strong advocates for the effectiveness of the Essential Eight. Businesses that take these strategies on board and strive to land on the optimum maturity level are simply better protected and more compliant with any laws around data protection.
We know that cybersecurity processes like application patching can feel like an overwhelming juggling act, which is why we’re here to help. We won’t just help you implement reliable patch management systems – we’ll uplift your entire cybersecurity posture to align with the Essential Eight.
Chat with one of our team if you’re looking for guidance on your journey to powerful and enduring cybersecurity. We’re here to help!
When he’s not writing tech articles or turning IT startups into established and consistent managed service providers, Peter Drummond can be found kitesurfing on the Gold Coast or hanging out with his family!