Here’s a sobering stat from IBM: on average it takes a company 197 days to discover they have been hacked. Once discovered, it takes 69 days to contain the breach.
That’s a long time. Can you imagine the havoc a hacker can wreak in that period? No wonder the financial repercussions of a data breach are so high and increasing every year. It’s a lucrative game for cybercriminals, and you don’t want to be on the wrong side of that particular balance sheet! There’s non-financial damage too, in the form of reputation loss and legal ramifications, both big burdens for a business to bear.
Anticipation and quick addressing of a cyber-attack are key to containing the fallout. Knowledge is power in this instance, so the more you know about how a hacker goes about their business, the better prepared you can be to stop them entering your systems.
We’ve given you a breakdown below of the standard hacking cycle that’s normally followed.
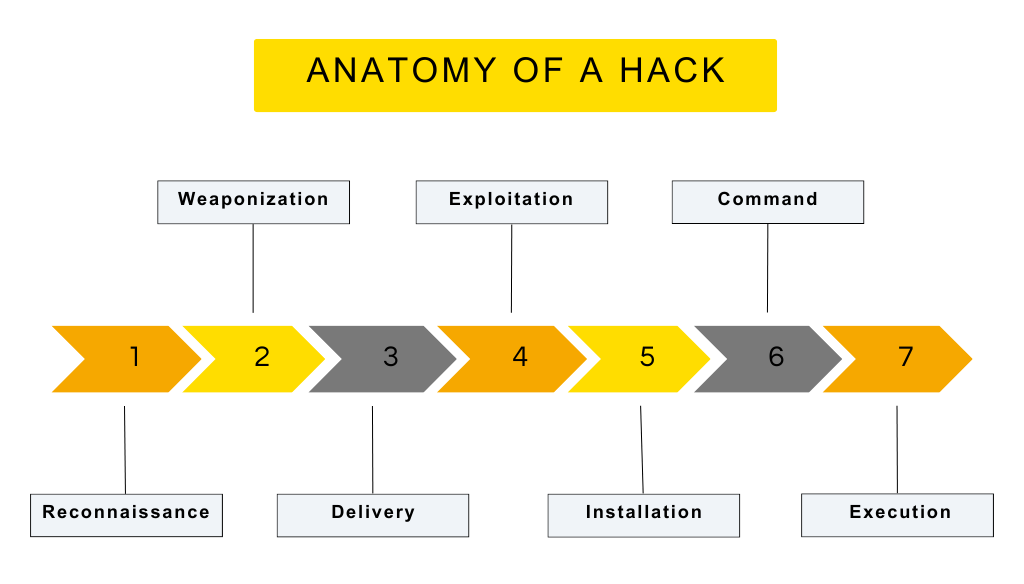
The Hacking Cycle
-
Reconnaissance and Gathering Intelligence
This initial phase involves the attacker identifying a vulnerable target, collecting information about it and figuring out how they can exploit it. All it takes is one point of entrance, and they’re doing their best to find it at this stage. This not only involves scanning for weaknesses in the networks and systems, but also getting to know who’s important in a company and who they do business with. This helps them employ techniques like social engineering and phishing.
-
Weaponization – Creating the Attack Vector
They’ve gathered the data and information, now the hackers figure out the best path to compromising their target’s systems and data. This phase is critical for preparing the actual means of attack. They’ll look at the software and systems and see if they can use code to break down any barriers in place. Unpatched or outdated software is particularly at risk.
They will also spend this phase of the attack collecting the tools they need to exploit vulnerabilities once they’ve gained access.
-
Delivery – Distributing the Weapon
The target has been identified – their names and roles within the organisation are known to the hackers and they zero in on them by delivering the weaponised threat. This could be in the form of a phishing email, ransomware, malware or a fake landing page to try and glean login credentials and passwords.
The users aren’t aware of or expecting malicious links to come through to them. Meanwhile, the hackers wait and see if their efforts will be rewarded.
-
Exploitation – Breaching Defences
This stage marks the initial breach of security, allowing the attacker to execute their malicious payload. The breach is essentially a success now – they’ve bypassed defences and can start making the most of their endeavours. This is probably the most important stage for the hackers, as they now have access to your organisation and can spend time familiarising themselves with it. They explore the infrastructure, get an idea of its traffic flow and figure out what other connected systems they can get access to.
-
Installation – Ensuring Persistent Access
Following a successful breach, attackers establish a foothold within the network. They want continued access, and creating a persistent backdoor will help them achieve this. Disabling security measures, creating administrator accounts and even activating remote desktop access on servers are all part and parcel of this installation phase.
-
Exercising Command and Control
With unrestrained network access at their fingertips, the attacker moves into the command and control stage. They’re in charge of the applications and systems, with the ability to glean user information and even perform functions on behalf of unknowing team members. They have the power to remotely manipulate the compromised systems, issuing commands, stealing data and further spreading their presence across the network.
-
Actions on Objectives – Executing the Goal
The attackers went into this project with an objective or objectives, and in this stage, they set about achieving those. The objectives vary but may include installing ransomware, initiating Distributed Denial of Service (DDoS) attacks, system disruption or extracting as much personal information as possible. While financial gain is usually at the core of cybercrime, the hackers may also be motivated by political or social reasons.
Disrupting the Cycle
All businesses today are at risk of getting hacked – to the point where it’s not when, but if, your company falls into the sights of cybercriminals. How do you protect yourself?
A proven and effective means of improving your cybersecurity posture and thwarting attacks is to enlist the services of a managed IT services provider. An MSP places a huge importance on keeping your company and client data safe. They’ll ensure your software is updated at all times, all the necessary security patches are installed and robust firewalls are in place. They monitor your network and systems 24/7 to pick up on threats before they snowball, and they can help educate your staff on cybersecurity best practices.
Your MSP will also implement a strategic incident response plan to revert to in the event of a cyberattack. This will include clear response steps to minimise the negative effects of the hackers. They’ll ensure all data is backed up and can be easily accessed if your systems are compromised.
An MSP will keep you safe, keep you compliant with the relevant data protection regulations, and help maintain productivity and efficiency in your business. Why not talk to one today? Smile IT help businesses all across Brisbane and Australia improve their cybersecurity defences. Get in touch with us now and we’ll answer all your questions!
When he’s not writing tech articles or turning IT startups into established and consistent managed service providers, Peter Drummond can be found kitesurfing on the Gold Coast or hanging out with his family!