The wild world of cybersecurity continues to throw curveballs at businesses and their data with the growing prevalence of crypto ransomware.
This malicious software, or malware, sneaks into your computer and locks up the files on there with some serious encryption so you can’t use them. A ransom is then demanded for the removal of the malware and the return to normality of your computer. The ransom is often in the form of a cryptocurrency, such as Bitcoin, due to its anonymity.
The Five Stages of a Crypto-Ransomware Attack
The cyber-attack typically follows this process:
1. Installation: The malware can get into your computer through emails with malicious attachments, drive-by downloading from an infected website and even through social media messaging applications. Once it installs itself, it sets up keys in the windows registry. Then whenever you start up your computer, the malware gets set up too.
2. Criminal Server Contact: The ransomware connects with the headquarters service run by the criminals.
3. The Handshake: The ransomware on your computer and the main server perform a intricate and unique handshake. A pair of cryptographic keys are generated, one on your computer and one on the main server.
4. Encryption: The ransomware on your computer begins to encrypt all the files on your computer.
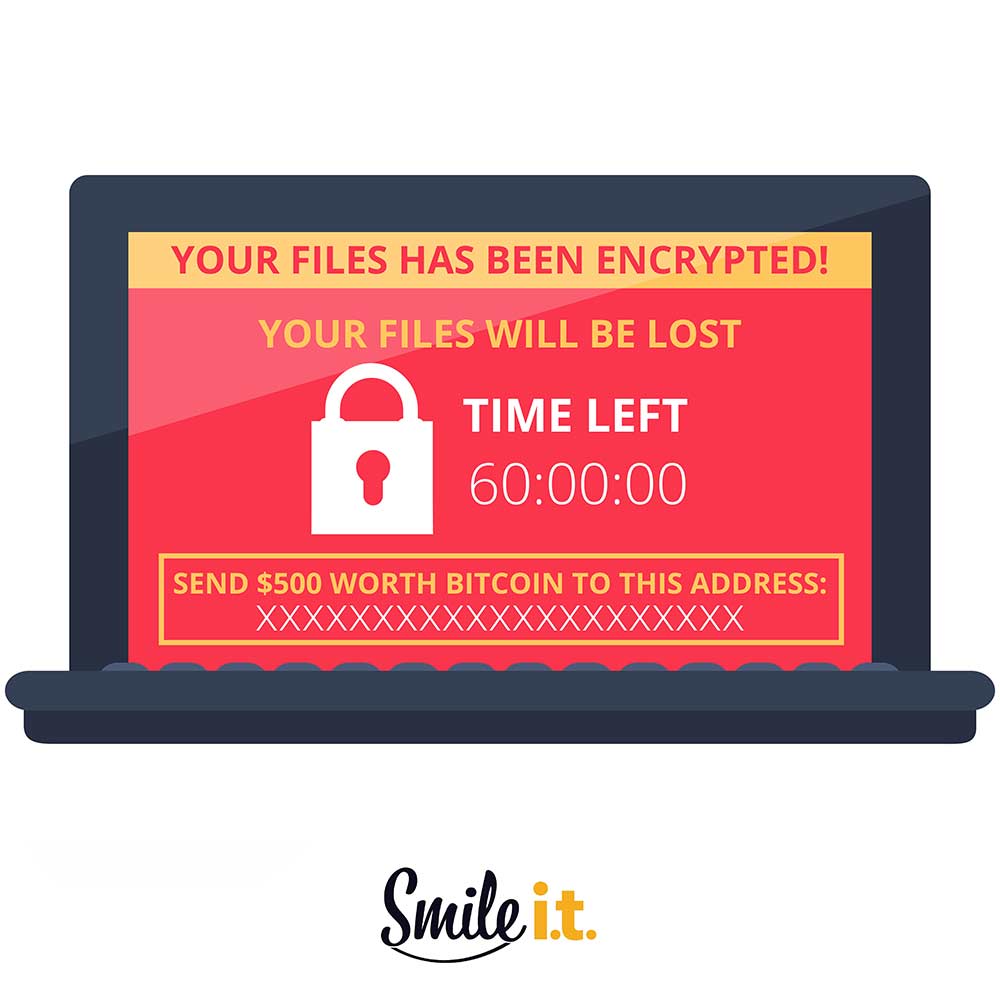
5. Extortion: The hacker wants to collect their ill-gotten dues. Your computer has now been hijacked and you’ll receive a message splashed across your screen with a ransom demand and how to pay it. You’re normally given a time frame in which to pay it or all your files will be destroyed.
Why is Crypto Ransomware on the Rise?
One of the reasons is that people are working remotely more, blurring the lines between office tech and home tech. Home networks are harder to control than office ones. There are more shared devices and people using the network are not employed by the same company. You can also have situations where a child uses a device and unknowingly clicks on the wrong link to download malware.
Crypto ransomware is increasing because it’s very lucrative for the criminals. The truth is, people are paying the ransoms and the gangs are making their money out of it. There’s the fear of losing their data and processes forever, plus the time restriction adds an element of panic to the whole situation. Although law enforcement agencies advise against paying the ransom, many people do. As a result we’re seeing more and more of this kind of hack.
How to Stay Safe from Crypto Ransomware
If your company experiences a crypto ransomware attack you potentially lose your data, you endure a lot of downtime and you could end up paying a hefty ransom fee. This is a situation you want to avoid, and here is how you can avoid potentially catastrophic situations:
- Backup your files regularly. A cloud backup is advisable, as is a physical backup in a location not connected to your network. This means you’ll always have unaffected copies of your data to turn to in case of an attack.
- Restrict the write permission policy for all your file servers.
- Use advanced endpoint protection to identify malicious traffic and malware variants.
- Educate your team on the potential signs of security threats. Strange popups should be avoided. They should be able to recognise emails with dodgy attachments.
- Anti-virus software as well as all operating systems should be kept updated at all times. All critical security patches should be applied.
- If an attack is suspected, disconnect the device immediately from all networks.
Being aware of and prepared for a crypto ransomware or other malware attack is a huge first step in mitigating the damage done. We all know the importance of business continuity, so having decent defences in place and a rock-solid backup and recovery plan will assist in strongly reducing downtime.
Smile IT’s Enterprise Crypto Ransomware Defences
Having a Managed Service Provider like Brisbane company Smile IT take care of your IT gives you a number of advantages when it comes to your cyber security. As well as seamlessly backing up all of your data, we offer 24/7 monitoring of your IT systems to ensure problems are detected before they become an issue.
We also use advanced endpoint exploit prevention software from leading global companies such as Acronis and Sophos. This ensures the best cyber security tools on the planet are put to work protecting your business and its data.
Got any questions about crypto ransomware and how it could affect your business? Please get in touch with the Smile IT Team. We’re a Brisbane MSP committed to leading the way when it comes to cyber security. We’d love to help protect you from the latest threats out there.
When he’s not writing tech articles or turning IT startups into established and consistent managed service providers, Peter Drummond can be found kitesurfing on the Gold Coast or hanging out with his family!