Smile IT recently undertook a Cyber Security Assessment for one of our clients, with an aim to evaluate the effectiveness of their cyber defence controls. This case study is designed to provide an idea of how we adapt our assessment approach to individual companies. The aim is to provide relevant results and recommendations that strengthen cyber defences while balancing the interests of the company, their customers and other relevant stakeholders.
The approach we took to this assessment is what you’d expect if you got a ‘Big 4’ firm to do a security assessment, but without the massive price tag. This is more than just a software scan, it’s a business risk approach that is part of our LEAN consulting program.
Our assessment provides intuitive, relevant results designed to cater towards a recurring incremental review service. They can be used to benchmark your process and security improvements against agreed maturity ratings which is extremely useful for compliance reports to boards, investors or other stakeholders.
The Company
For our assessment the company was classified as a small to medium sized organisation with reasonable IT and cyber-security expertise. The Centre for Internet Security (CIS) would classify this as a ‘Implementation Group 1 organisation’. With this classification our review could cover the 41 controls relevant to IG1 organisations.
Some points about the company are:
– Reasonable IT and cyber-security expertise;
– Utilise sensitive customer and survey data;
– Low level of technical complexity means most risks would have a minor or moderate impact;
– Excessive cyber-security controls would result in inefficiency, hence a need for security that doesn’t place undue pressure on company resources.
Our Approach
The review entailed two modes of enquiry:
– Interviews with key staff regarding cyber security related processes and controls, with requests for examples of supporting evidence where available;
– The running of specialised network and security scanning software against the company’s equipment and networks in order to identify any cyber security weaknesses.
As an IG1 organisation, the following were reviewed using the 41 specific controls recommended by CIS:
Basic:
– Inventory and Control of Hardware Assets
– Inventory and Control of Software Assets
– Continuous Vulnerability Management
– Controlled Use of Administration Privileges
– Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers.
– Maintenance, Monitoring and Analysis of Audit Logs.
Foundational:
– Email and Web Browser Protections
– Malware Defences
– Limitation and Control of Network Ports, Protocols and Services
– Data Recovery Capabilities
– Secure Configuration for Network Devices, such as firewalls, routers and switches
– Boundary Defence
– Data Protection
– Controlled Access based on ‘Need to Know’
– Wireless Access Control
– Account Monitoring and Control.
Organisational:
– Implement a Security Awareness Training Program
– Application Software Security
– Incident Response and Management.
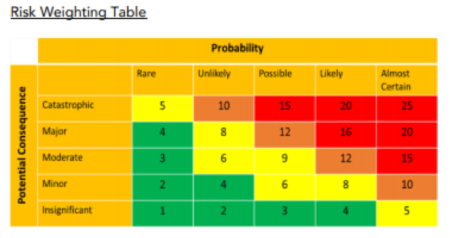
Risk Scoring:
The cyber security controls were assessed on a risk-weighted basis in order to provide a view of security risks as they pertained to the company. The following table provides the scoring system used for risk assessment:
The Findings
We divided our results into two categories, ‘Cyber Security Processes’ and ‘Key Technical Findings’. Most of the risks we assessed were either minor or moderate in impact.
The Key Technical Findings identified that there were no significant security risks. We developed an in-depth Security Risk Report documenting the assessment and scan results which we provided to the client for their reference.
Most of the ‘Cyber Security Processes’ we identified were also of moderate to low risk. Importantly, most of these could be mitigated through some simple changes to the security configuration and the delivery of user security awareness training.
We were able to use our findings to recommend a number of key actions that would address any weaknesses and improve the company’s cyber security now and moving forward.
What about your organisation? Are you confident in your cyber security? Do you have a Chief Security Officer in place? Are you well-placed to recover quickly after a catastrophic cyber incident? A Smile IT cyber security review will answer a lot of questions for you, secure your defences and help keep your company and client data safe.
Get in touch if you have any more questions, we’d love to help out.
When he’s not writing tech articles or turning IT startups into established and consistent managed service providers, Peter Drummond can be found kitesurfing on the Gold Coast or hanging out with his family!